The Bybit hack has exposed a glaring blind spot in Web3: how do you trust the code you’re signing if the front end itself is compromised? Binary Transparency is the missing puzzle piece ensuring code integrity from developer to end-user. And with Walrus + Sui, we not only fix these vulnerabilities but also unlock a new frontier of unstoppable dApps and AI-driven experiences.
BTW: Here’s the link to my Substack to stay posted:
The Day Web3 Nearly Broke (Again)
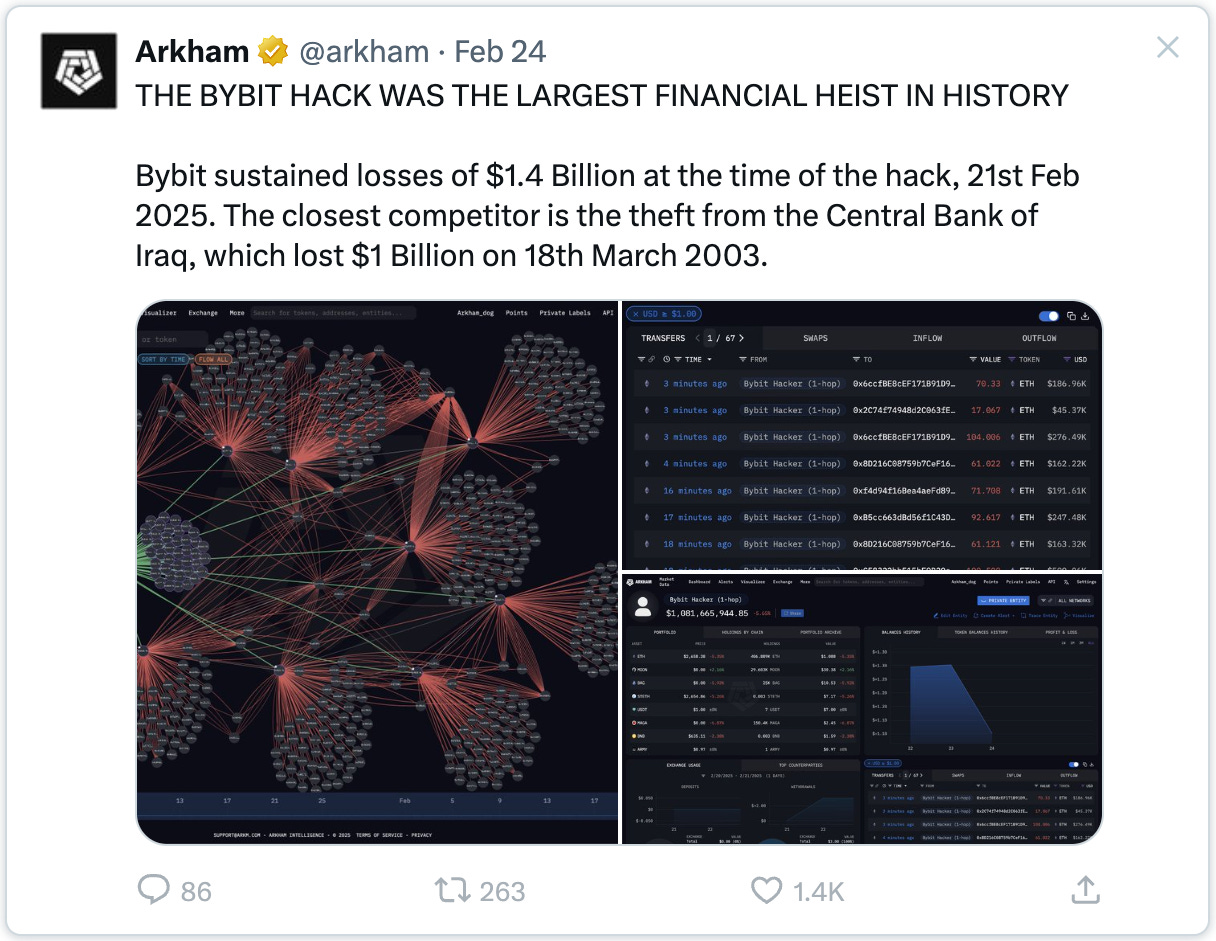
Imagine waking up and realizing $1.4 billion might vanish because someone manipulated just a few lines of JavaScript code.
On February 21, 2025, that nightmare became reality for cryptocurrency exchange Bybit.
In a matter of minutes, attackers drained 401,346 ETH, along with 90,376 stETH, 15,000 cmETH, and 8,000 mETH from what should have been an impenetrable cold wallet.
This wasn't just another hack.
It was the largest single crypto heist in history, eclipsing even the infamous Mt. Gox and Ronin network breaches.
And it happened not by cracking encryption or stealing private keys.
Instead, it exploited something far more fundamental: the broken trust model underlying how we interact with blockchain technology.
Behind the Bybit Hack: Fragile Foundations
If you want to talk about a deviously simple piece of evil genius, this is it.
The North Korean Lazarus Group never bothered to smash through Bybit’s own defenses. Instead, they waltzed through the back door by compromising a Safe developer’s credentials.
A move that gave them the keys to Safe’s AWS S3 bucket, where the multisig web interface lived.
All they did was inject some malicious JavaScript that only kicked in for specific targets, like Bybit’s cold wallet.
So when Bybit’s executives plugged in their Ledger hardware wallets on what looked like the official Safe site, they saw exactly what they expected: a routine 30,000 ETH transfer to a warm wallet.
URL was right.
Destination address was right.
Everything looked normal.
But behind that pristine façade, the sneaky code “masked” the real payload: an upgrade of Bybit’s multisig contract into a malicious version packed with “sweep” functions.
The moment the signers approved that final transaction—boom, the wallet was effectively hijacked. The hackers triggered those hidden backdoors and drained the entire stash in minutes.
The crazy part? The blockchain itself wasn’t the problem.
This was all about the fragile bridge between humans and a trustless network. Specifically, the front-end we rely on to interpret and confirm complex on-chain ops.
When that front-end gets poisoned, even the best hardware wallets and multi-sig logic won’t save you.
The Front-End Blind Spot Nobody Talks About
We love to brag about blockchains. “Immutability,” “decentralized consensus,” all the buzzwords.
But here’s the awkward truth: nearly 100% of users, even the biggest exchanges and dev teams, interact with these “trustless” systems through centralized web interfaces.
That neat little HTTPS lock? It just means your connection is secure in transit. No one’s eavesdropping or tampering with data as it travels between you and the server.
But it says nothing about whether the server itself has been compromised or if it’s unknowingly serving up malicious code.
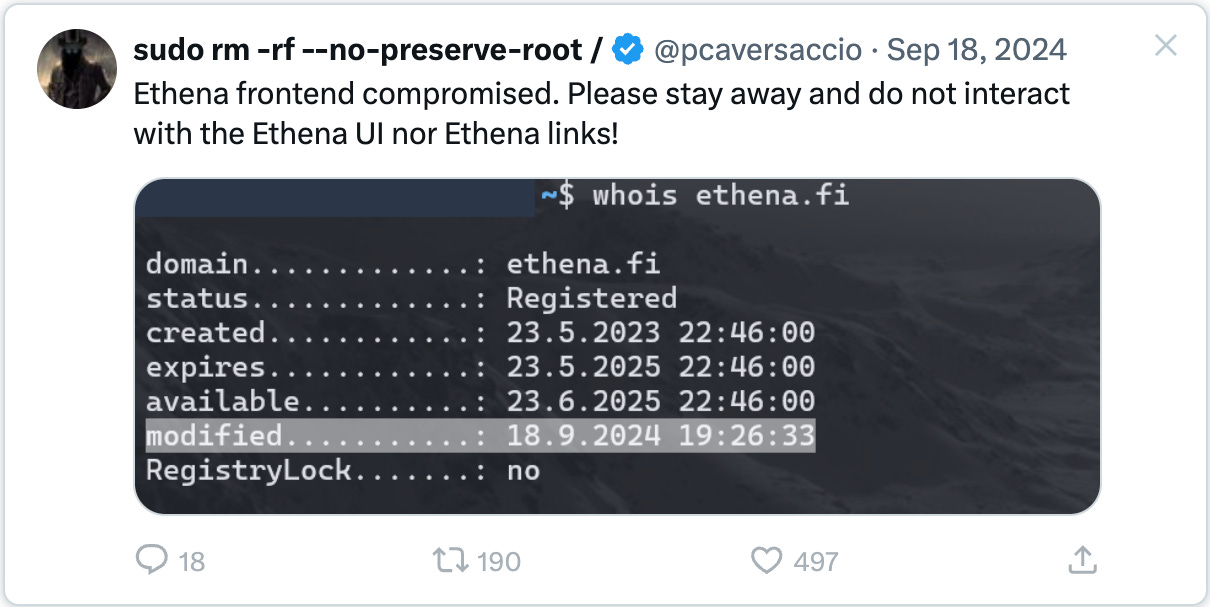
That’s exactly where Bybit’s Safe interface fell short.
It lacked Subresource Integrity (SRI) checks, a basic yet crucial web security measure that ensures JavaScript files haven’t been altered before they reach your browser.
Without it, attackers could inject malicious scripts into the interface, and users would have no way of knowing.
Lacking that, the injected code silently worked its magic.
Attackers designed the script so the UI showed harmless transaction details while sending completely different instructions on-chain.
And because Bybit’s procedures assumed “the front end must be legit,” nobody demanded a second, independent check.
One security pro put it bluntly: “Front-ends should always be assumed compromised. If your signing process doesn’t account for that, you’re basically signing your own doom.”
Terrifyingly, this isn’t some radical new exploit.
Last October, DeFi platform Radiant Capital got fleeced for over $50 million in a nearly identical manner.
Hackers slipped malware into a fake contractor resume, then used it to tamper with the Safe interface. Bybit’s fiasco just ramped up the same technique to a colossal scale.
This cuts right to a core contradiction in Web3: we’ve got these unstoppable, trustless protocols, but everyone accesses them through a web front end that’s basically “trust me, bro.”
No matter how bulletproof your chain or contracts are, if the browser code is crooked, it’s game over.
What we need urgently is a way to confirm the code in your browser is exactly what the devs intended you to run.
In other words, we need binary transparency.
Binary Transparency: The Missing Piece Nobody Talks About
At its core, Binary Transparency is a public, tamper-evident log of every legitimate code release.
Instead of blindly trusting that the update you got is legit, you (or your wallet, or an automated checker) verify that the code’s cryptographic “fingerprint” actually exists in the public record.
Think of it this way: if Bybit had required Safe’s front-end code to show up in a well-audited transparency log, that malicious JavaScript injection would’ve stood out like a clown at a black-tie dinner.
The script wouldn’t match any known “official” release, so any attempt to slip it into Bybit’s environment would raise a screaming alarm.
If that had happened, there’s a good chance that 401,000 ETH would still be in Bybit’s wallet today instead of in Lazarus Group’s pockets.
The beauty is that everyone can see this log. It’s not some hush-hush registry hidden behind a corporate firewall.
In the same way we can check a product’s authenticity code or a software’s signature, we can now check whether a given binary or web update is the exact build the developer promised.
No hush-hush midnight updates. No invisible “special versions” for high-value targets. You either match the official entry in the log, or you’re a malicious outlier.
This is Why Binary Transparency Isn’t Optional Anymore
You might be thinking, “Sure, that might’ve saved Bybit. But is this ‘transparency log’ idea really that big a deal?”
Short answer: absolutely. Because the Bybit hack wasn’t just a one-off accident.
We’ve seen this script play out with DNS hijacks on PancakeSwap and Cream Finance, where a hijacked domain served fake sites that looked perfectly real.
We’ve seen front-end injections hammered onto MyEtherWallet users. We’ve even seen Trojaned browser extensions passing themselves off as legit tools.
And through it all, the biggest irony stands: while we celebrate unstoppable, trustless blockchains, hackers keep strolling right in through the front-end, seizing control at the website layer.
So how does Binary Transparency help against these attacks, like DNS hijacking or malicious extensions?
The same way it would’ve saved Bybit.
If every front-end release, every bit of code, and every update is logged publicly with a unique cryptographic fingerprint, any tampered version lacking that “official” mark triggers an immediate red flag.
Even if a DNS hijack points you to a spoofed site, or a Trojan extension claims it’s the real thing, none of that code would appear in the public record as a valid release.
Your wallet or your system checks the log, sees an unrecognized hash, and instantly says, “Nope, something’s off.”
That’s why the “transparency log” concept is so huge. It addresses the fundamental gap between “unhackable blockchain” and “vulnerable front-end.”
It shines a big spotlight on any code that dares deviate from what the developers “actually” shipped, whether that deviation happens through DNS spoofing, server-side injections, or even supply-chain sabotage.
And that naturally leads us to a bigger question: “How do we actually implement this in a decentralized context?”
Walrus: The Binary Transparency Layer for Web3
So we’ve made a pretty loud case for why front-end security can’t be an afterthought. The question is, how do we actually fix it?
How do we move past the old world where a single compromised JavaScript file can turn a billion-dollar wallet into an attacker’s playground?
The answer isn’t just better security practices or more audits. It must be infrastructure-level guarantees.
The answer is a system that makes it impossible for a compromised front-end to go unnoticed.
That’s where Walrus comes in. Think of Walrus as the trustless “binary transparency” layer for the internet.
When you upload a file, be it HTML, JavaScript, or an entire OS installer, Walrus creates a cryptographic fingerprint (like a SHA-256 hash) and records it on the Sui blockchain.
That means if someone later tries to slip in a malicious version, its fingerprint won’t match the ledger entry, instantly flagging the swap.
To achieve this, Walrus splits each file into chunks, erasure-codes them across independent storage nodes, and collects cryptographic proofs from those nodes confirming the chunks are correct.
The resulting availability certificate is then finalized on Sui.
No single server or compromised dev credential can secretly replace a file without revealing a hash mismatch in the blockchain record.
If you run a front-end from Walrus (“Walrus Sites”), every asset is verified against its on-chain hash before serving.
Any mismatch raises an error, thwarting front-end injection attacks like the one that blindsided Bybit.
The same mechanics apply to big software packages: once the code is published and logged, users can confirm they’re downloading exactly what the developer intended.
Had Bybit’s multisig interface been stored on Walrus, the malicious JavaScript injection would have been caught the moment it landed.
Hackers can’t just push a fraudulent hash without the chain noticing the discrepancy.
In a nutshell, even if an attacker cracks a dev’s credentials or hijacks a hosting server, they can’t pass off their tampered file as the legitimate version.
Walrus enforces an end-to-end audit trail that calls out any hidden updates. This is the difference between blind trust and verifiable security.
With Walrus, front-end exploits like Bybit’s aren’t just difficult, they become fundamentally impossible.
You either serve the correct files, or the entire system calls you out.
So you’ve got Walrus guaranteeing code integrity on the storage side.
Now, pair it with Sui’s Move-based contracts, explicit upgrade rules, and on-chain enforcement, and you get an even more rock-solid system.
Walrus + Sui: A Bulletproof Combo for Web3’s Frontlines
So Walrus makes front-end integrity practically untouchable. But ensuring bulletproof security also demands a blockchain that does “smart contracts right”.
Especially when it comes to preventing fiascos like ad-hoc proxy upgrades (‘delegatecall’ nightmares, anyone?).
It’s not that the EVM is useless or that human error doesn’t matter.
But as the Bybit story made painfully clear, an ecosystem reliant on fragile scripts and “just trust me” upgrade paths is destined to get blindsided.
Sui, on the other hand, was built from the ground up to avoid these pitfalls.
Sui Move-based smart contracts enforce explicit invariants. This means that no random third-party code can rewrite your entire wallet logic through a single misguided “approve” click.
By implementing typed modules and structured upgrades, Sui makes it much harder for an attacker to slip in a malicious contract swap without setting off alarms.
When you pair Walrus’s tamper-evident front-end hosting with Sui’s more robust contract layer, the synergy helps close every angle.
That’s the “bulletproof combo”.
Walrus locking down all incoming code at the data layer, and Sui’s structured modules locking down contract logic at the execution layer.
And because both revolve around publicly verifiable code references, you get a one-two punch that prevents front-end injection and proxy exploitation.
Plus there’s also another powerful feature in Sui’s toolbox that often gets overlooked: native multi-signature (multi-sig) support.
Native Multi-Sigs: The Extra Layer Institutions Need
Most blockchains force you to rely on custom smart contracts for multi-sig wallets. Not Sui.
On Sui multi-sigs are implemented directly at the protocol level rather than as a smart contract.
Sui’s built-in cryptography module checks each partial signature, sums up their weights, and approves or rejects on the spot.
Not only does this reduce complexity, but it also cuts out the “oops, we forgot to verify this corner case in our contract” situation.
Sui’s CLI and SDKs (TypeScript, Python, etc.) come with official commands and methods to generate multisig addresses, sign transactions, and combine partial signatures.
Because it’s all in native Rust code under the hood, you’re not messing with custom scripts that might break or be riddled with logic bugs.
The threshold logic is straightforward: sum the valid signatures’ weights, compare to the threshold, done.
Because Sui itself verifies whether enough valid signatures are present for each transaction, the usual single-key meltdown scenario also doesn’t apply.
Why does this matter so much for future supply chain attacks?
Because one of the best ways to protect high-value operations (like admin tasks for institutional wallets) is to require multiple, independent approvals.
If your interface or even one signer’s environment gets compromised, it’s not game over.
For high-stakes transactions, like upgrading a contract or rolling out major changes, you can set a 2-of-2 or higher threshold.
More importantly, you can make sure those signatures come from different apps or stacks.
In practice, if you need to authorize a transaction, Sui’s native multi-sig framework can ensure each admin signs from two distinct environments.
If either environment flags malicious code or sees a mismatch in the front-end, the transaction fails.
For institutional players looking to prevent the kinds of calamities we saw with Bybit, Sui’s native multisig is a game-changer.
Requiring two or more signers from different devices or software stacks, especially in a high-stakes environment, cuts off the attack vectors that rely on tricking just one front-end or persuading just one user to sign an exploit-laden transaction.
It complements Walrus’s front-end integrity checks and Sui’s explicit contract invariants by making sure no single compromised signer can unilaterally push malicious upgrades.
This layered approach brings the entire system closer to truly trustless security.
Put them all together, and you’ve got a security perimeter that’s actually worthy of the billions of dollars that flow through DeFi.
Now, imagine how this level of verifiable code and enforceable invariants scales when AI starts writing most of our dApps.
That’s where we quickly realize why secure, transparent storage and robust chain logic matter more than ever.
AI Is Here, and We’re Not Ready
Across every industry, AI is devouring tasks we once thought uniquely human.
As these AI agents gain autonomy, they don’t just read a single website or file a simple transaction.
They juggle countless bits of personal data, process instructions from multiple sources, and sign on-chain operations with minimal human oversight.
If you think a malicious front-end can cause havoc, imagine an AI agent wired to billions in assets, trusting every data source it’s fed.
That’s a whole new level of risk. And this is where binary transparency becomes indispensable.
By logging every version of an AI model (plus its training data and code) in a tamper-proof ledger, we give ourselves a real shot at spotting poison before it’s too late.
If a “mystery build” shows up on a model hub without a matching on-chain record, or if the code and data used to generate a new version don’t line up with official logs, alarms go off.
The entire AI pipeline, from dataset to final deployment becomes auditable. And that’s precisely the level of authenticity we need if we want to trust these systems at scale.
With AI’s capacity for large-scale automation, a single compromised model can cause a level of havoc that makes even a $1.4B crypto hack look quaint.
That’s why an infrastructure that merges bulletproof data integrity with unstoppable on-chain logic is quickly evolving into a basic requirement.
Walrus and Sui: The Infrastructure AI Demands
Walrus isn't just decentralized storage, it's Web3's data integrity backbone for the AI era.
Imagine a machine-learning model that needs access to a user’s encrypted dataset. Walrus pins that dataset to a cryptographic fingerprint on-chain, so any sneaky alteration triggers an immediate mismatch.
With Walrus, every data asset comes with an instant cryptographic guarantee, letting AI agents independently verify authenticity at runtime.
Meanwhile, every decision the AI makes can be logged immutably, preserving a transparent audit trail for compliance and post-mortems.
It’s a radical shift from “the AI says so” to “the AI says so, and we can prove it’s working off authentic data.”
Sui complements this data integrity perfectly by functioning as AI's global coordination layer.
Sui’s Move-based environment ensures AI-driven actions obey explicit rules around identity, access control, and secure data exchange.
Because Sui handles contract upgrades with typed modules and strict invariants, there’s no “delegatecall fiasco” leaving the door open for a quick malicious swap.
You can tie down how AI updates get pushed on-chain, which user data they’re allowed to touch, and how keys are managed across different nodes.
In practice, that means an AI agent can manipulate complex objects, sign transactions, or coordinate tasks with other agents.
But only within the bounds you define. If it tries stepping outside, Sui’s logic calls a hard stop.
By combining Walrus’s bulletproof data integrity with Sui’s verifiable contract controls, you get a robust pipeline for AI.
It runs code exactly as intended, interacts with data that’s guaranteed authentic, and executes contract logic that can’t be hijacked by a stray line of code.
Locking the Front Door Once and For All
The Bybit hack was a gut punch, but it taught us an important lesson: trustless blockchains are only as secure as the front ends we use to access them.
Until we eliminate that gaping blind spot, even bulletproof protocols will remain sitting ducks.
As we hurtle toward an era where autonomous agents make million-dollar decisions in seconds, that unstoppable automation demands unstoppable security.
And with Walrus and Sui working in tandem, we’re building an ecosystem where malicious code can’t hide, AI models can’t fake their origins, and unstoppable dApps actually live up to that promise.
Walrus gives us cryptographic proof that the code (and data) we run is exactly what developers intended, no backdoors allowed.
Sui enforces the chain logic, typed upgrades, and multi-sig guardrails that keep your assets.
When you consider how fast AI is spreading, an integrity layer like Walrus plus a bulletproof on-chain execution layer like Sui isn’t a “nice-to-have”, it’s the only way forward.
So, let this be the final line in the sand: no more half-measures.
The future of Web3 belongs to those who hardwire trust at the protocol level, ensuring code is genuinely verifiable from developer to device.
We have the tools; now we just need to use them.
BTW: Here’s the link to my Substack to stay posted:




















Check once DM sir
Powerful stuff! Sui is doing a great job intersecting the needs of the future and the ever evolving technology of today. Keep up the innovative work!